Strengthening Wi-Fi security at the hardware level RFSTAR RF-WM-3220B1 W-iFi module
Strengthening Wi-Fi security at the hardware level
If you’re an Internet of Things (IoT) designer, you’re probably often challenged to do more with less when it comes to security, constantly looking for new ways to protect your products against an ever-growing list of threats with lean system resources and perhaps limited experience.
Knowing that these struggles are very real, in this post I’ll outline a few top IoT security risks and common misconceptions on how to address them. I will also provide an overview of how new CC3220SF Wi-Fi module RF-WM-3200B1 give you more tools to help address security challenges through a novel architecture and rich set of integrated security features.
Are there IoT applications that don’t need to implement security measures?
Any device that connects to the internet may be vulnerable to local or remote attacks. Attackers can target almost any connected device to try and steal manufacturer intellectual property stored in the system, gain access to user data, or even maliciously manipulate the system to compromise users or attack third parties online.
As demonstrated by the major distributed denial of service (DDoS) attack late last year, labeled by experts as the largest of its kind in history, even seemingly harmless products such as home digital video recorders (DVRs) can be maliciously infected and used as “botnets” to halt operations for third-party entities. The attack last year affected services such as Twitter and PayPal, but similar attacks could potentially target large smart infrastructure technologies such as electric grid systems. According to a 2016 study conducted by Kapersky Lab, a single DDoS attack can cost an organization more than $1.6 million to resolve.
Recognizing these threats,RF-star's CC3220SF Wi-Fi module integrates a host of powerful, multilayered and hardware-based security features to provide you with powerful tools to help protect products from attacks such as local or remote packet sniffing, man-in-the-middle (MITM) server emulation, hostile takeovers via over-the-air updates, remote file manipulation, data and software theft, intellectual property (IP) cloning, and many more. Watch the below video to learn more about these tools:
Should IoT security features primarily focus on Wi-Fi and internet-level encryption of packets sent over the air?
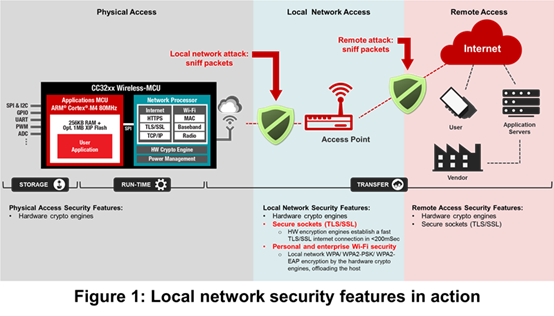
Having strong Wi-Fi (Advanced Encryption Standard [AES]/Wired Equivalent Privacy [WEP]) and internet-level (Transport Layer Security [TLS]/Secure Sockets Layer [SSL]) encryption is critical to help prevent local and remote network-packet sniffing, respectively. But these measures alone may not be enough to fend off hostile takeover attempts or provide full protection against theft of IP, code, data, keys and identity information stored and used in a connected system. Figure 1 illustrates these measures in action.
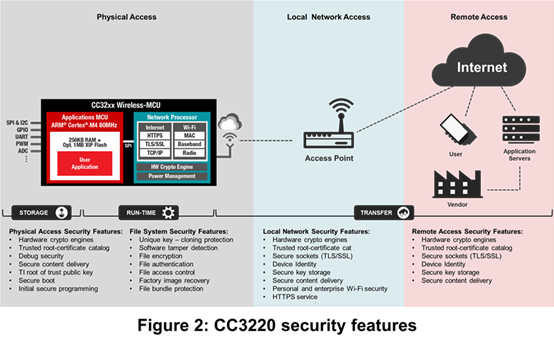
The CC3220 Wi-Fi module actually integrates more than 25 additional security features to help provide tools that address potential threats from the larger end-to-end IoT landscape. Figure 2 portrays many of these features.
Do you need to use a high-end microprocessor unit (MPU) or dedicated secure element to effectively protect your products against potential risks?
While increasingly lean IoT system resources often present design challenges, you can still strive to target more robust security in MCU-based, bill of materials (BOM)-optimized systems. The first steps are to identify which system assets are at risk, where the potential exposure points exist and what threats you anticipate will put the system at risk. From there, you work to choose components that offer a wide range of integrated hardware-based security features, while offloading the host MCU.
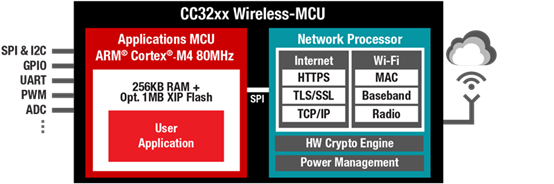
The CC3220SF Wi-Fi module sets out to give you these tools. The unique dual-core architecture (illustrated in Figure 3) runs both the host application and the network processing on a single chip to simplify the design. However, running these operations on two physically separate execution environments enables the chip to:
· Offload the processing of the device’s security functionality (including secure file system management) to the network processor and hardware cryptographic engines. This enables the million instructions per second (MIPS) and application MCU memory to be solely dedicated to the host application.
· Help reduce the firmware and network-management vulnerability for application-related risks by physically partitioning the programmable application MCU from the read-only memory (ROM)-based network processor